Private companies have access to more of consumers’ personal information than ever before, and customers expect that these organizations will protect their details and continually safeguard their privacy. However we see yearly examples of massive data breaches that endanger consumer personal information. Companies have to constantly evolve and adapt to combat the security challenges that come with managing data, or they risk massive financial consequences. So, how do enterprises protect sensitive personal information?
Enter Data Loss Prevention, or DLP. One of the cornerstones of modern cybersecurity, data loss prevention is a necessity for any company that handles sensitive information
(which, at this point, is just about every organization
!) Today we’ll dive a little deeper into what data loss prevention is, key reasons to have a strong DLP system in place, types of DLP, and implementing actionable DLP best practices at your company.
What is Data Loss Prevention?
Data Loss Prevention consists of a system of security tools and policies that constantly monitor and protect sensitive data to ensure it isn’t leaked, used improperly, or stolen. DLP spans across end-user activities like work apps, data and videoconferencing tools, as well as managed endpoint devices, and both on premise and cloud storage systems. These tools respond to risks of exposure or leakage of sensitive information in accordance with predefined policies, rules, and best practices to mitigate potential dangers.
Why is Data Loss Prevention Important?
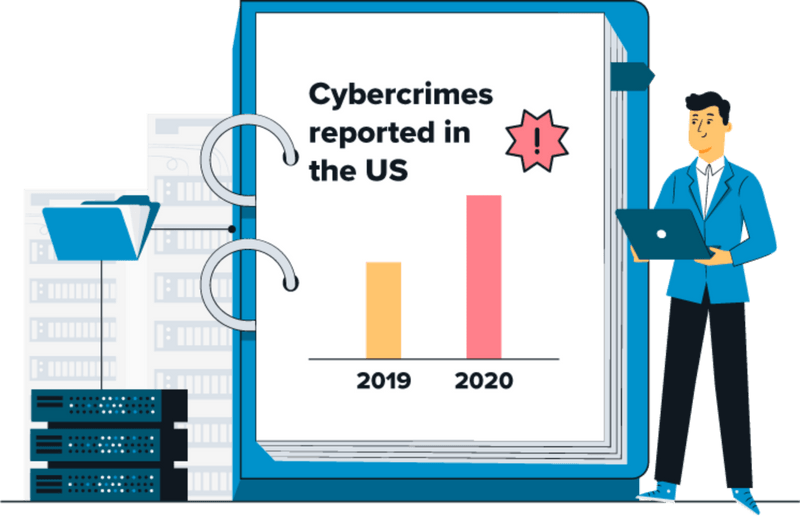
In today’s digitized economy data and customer information is worth its weight in gold. The creation of better products, customized user experiences, customer support and retention programs, and more is enabled by information that consumers give to companies. With the rise of the financial importance of customer data, and the fact that more of it is available than ever before, data theft and sale has emerged as a lucrative criminal industry. According to a recent study conducted by the FBI’s Internet Crime Complaint Center, the U.S saw over 761,000 reported cybercrimes in 2020, up 69
% from 2019. The financial ramifications of data leaks to companies are massive, making DLP more crucial than it has ever been.
DLP is also crucial for compliance purposes as organizations and governing bodies like the European Union continue to pass more stringent data management policies and regulations, like GDPR. Events like the Cambridge Analytica scandal have spurred lawmakers around the world to enhance regulatory precautions based around data handling and protection. Adopting a strong DLP strategy today is a great way for companies to stay ahead of government regulation and avoid potential financial liabilities down the line
Understanding Different Types of DLP
While all data loss systems are fundamentally aimed at preventing unauthorized information leakage, not all operate the same way. Today we’ll dive into three types of DLP: network, endpoint, and cloud.
Network DLP
Network data loss protection focuses on securing information in the internal network infrastructure of the organization. To do so it puts up a secure area around all the data on the move throughout the network, constantly screening and checking for sensitive information. From here, corrective actions are taken in accordance with rules and policies when risks for data breaches emerge. For example, a user tries to send confidential documents from a work account to an account outside of the organization. Provided they’re operating on a company network, the email could be flagged, blocked, or trigger an audit.
PROS OF NETWORK DLP
 Ease of management for all
devices on a given network
Ease of management for all
devices on a given network No device software required
No device software required
CONS OF NETWORK DLP
 Ease of management for alldevices on a given network
Ease of management for alldevices on a given network
Endpoint DLP
Rather than manage the security settings of the network endpoint DLP revolves around continually protecting the individual employee devices. Whether it’s a work
–issued endpoint or a BYOD, a computer, tablet, or mobile phone, active software constantly monitors the organization’s endpoints to maintain compliance. While this allows the company to continually protect their sensitive information it requires a lot of trust in their employees, as well as extensive hands-on device management that can prove difficult in a remote setting.

PROS OF ENDPOINT DLP
 Blanket security of all organizationdevices at all times
Blanket security of all organizationdevices at all times Network agnostic
Network agnostic
CONS OF ENDPOINT DLP
 Logistically intensive
Logistically intensive Potentially employee privacyconcerns
Potentially employee privacyconcerns Constant device management
Constant device management
Cloud DLP
As tech companies around the world continue to develop cloud native solutions and applications the need for new security tools and products has risen to the forefront. Today many cloud storage providers are building DLP tools into their infrastructure, protecting customer data before it enters the cloud. By encrypting or altering data before it enters the cloud organizations are able to protect their sensitive information while storing it remotely. Cloud DLP solutions have the flexibility to integrate with cloud storage solutions, constantly scan data in the cloud, conduct continued audits, and allow for easy, safe information transfer.
PROS OF CLOUD DLP
 Ease of use for cloud systems
Ease of use for cloud systems Works well for distributed
workforces
Works well for distributed
workforces Endpoint software not required
Endpoint software not required
CONS OF CLOUD DLP
 Reliant on cloud storage provider
Reliant on cloud storage provider
Three Actionable DLP Best Practices
Here are three quick tips to enhance DLP protocols.

Implement a unified and centralized DLP policy:
Rather than relying on case by case policy decisions create a uniform, replicable and enforceable DLP strategy that can easily be overlaid on any data loss scenario.

Classify data to promote efficiency:
Creating a rigorous and definite system of data organization for both structured and unstructured data to allow for constant monitoring according to pre–established taxonomies.

Increase organization wide buy–in:
A commitment to a strong DLP has to extend beyond just the IT department and CISO’s office. All parts of the organization need to adhere to policies and play their part in helping to keep sensitive data safe
 DLP is also crucial for compliance purposes as organizations and governing bodies like the European Union continue to pass more stringent data management policies and regulations, like GDPR. Events like the Cambridge Analytica scandal have spurred lawmakers around the world to enhance regulatory precautions based around data handling and protection. Adopting a strong DLP strategy today is a great way for companies to stay ahead of government regulation and avoid potential financial liabilities down the line
DLP is also crucial for compliance purposes as organizations and governing bodies like the European Union continue to pass more stringent data management policies and regulations, like GDPR. Events like the Cambridge Analytica scandal have spurred lawmakers around the world to enhance regulatory precautions based around data handling and protection. Adopting a strong DLP strategy today is a great way for companies to stay ahead of government regulation and avoid potential financial liabilities down the line

Ease of management for all devices on a given network
No device software required
 Ease of management for alldevices on a given network
Ease of management for alldevices on a given network
Blanket security of all organizationdevices at all times
Network agnostic
 Logistically intensive
Logistically intensive Potentially employee privacyconcerns
Potentially employee privacyconcerns Constant device management
Constant device management
Ease of use for cloud systems
Works well for distributed workforces
Endpoint software not required
 Reliant on cloud storage provider
Reliant on cloud storage provider



